Das Premium-CTF jetzt mit ohne Fanshop!
The CTF is over, thanks for playing! hxp <3 you! 😊
This is a static mirror, we try to keep files online, but all services will be down.
Join us on IRC! freenode | #hxpctf - Stalk us on Twitter @hxpctf
For the 36C3 Junior CTF click here
md15
by kirschju
Difficulty estimate: - medium
Points: round(1000 · min(1, 10 / (9 + [2 solves]))) = 909 points
Description:
* Hint: Remember, md15 is a reversing challenge. hxp recommends you stop reading crypto papers. *
After all this recent 0daying within the CTF community we figured eclipsing a standard deprecated hash function might be appropriate.
To comply with good scientific practice, the respective research paper is currently being peer-reviewed, and therefore secret. However, according to the PC, hyping the topic and publishing the abstract is okay-ish, so here you go:
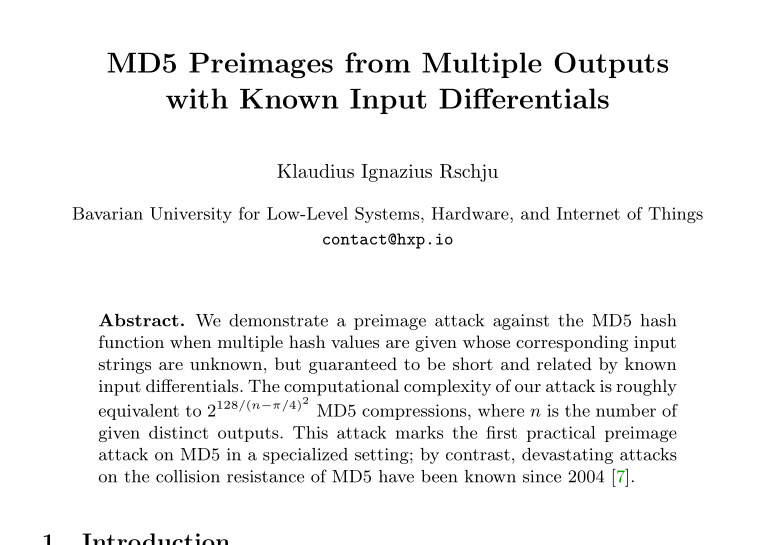
Clearly, 3 x MD5 == MD15, right?
Download:
Solved by:
| # | Team | Time |
|---|---|---|
| 🥇 | pasten | 2019-12-29 17:56:50 +0000 UTC |
| 🥈 | KJC+f0f+Spotless+SF+mhackeroni | 2019-12-29 18:38:10 +0000 UTC |

